
Any malicious software can endanger you and your device, but what makes this type of malware so unique?
Well, Ransomware is a type of malicious software used by cybercriminals to prevent you from accessing your data. The term "ransom" tells you everything you need to know about this pest. That malicious software can encrypt your computer and then demand a ransom to unlock it. And like any other virus, Ransomware also can spread over your network to shared drives, servers, attached computers, and other accessible systems once the initial infection has taken place. If the ransom demands are not met within the timeframe of cyber crooks, the system or the encrypted data is unavailable, or the software can delete your information and eliminate the decrypting key. So without a description key, it is impossible to decrypt the encrypted files. As a result, we can call Ransomware is a potential "nightmare" for unprepared IT peoples.
Ransomware Statistics
* Last year, there were over 304 million ransomware attacks worldwide. Every 11-14 seconds, a new organization is attacked.
* Encrypting data was successful in 73% of all ransomware attacks.
* 55% of attacks targeted businesses with 100 or fewer employees. 75% of attacks targeted companies with less than $50 million in annual revenue.
* Microsoft reports that nearly 97% of all infections in Ransomware take less than 4 hours for their target to be successfully infiltrated. The fastest can take over systems in less than 45 minutes.
* Over the past year, downtime caused by Ransomware increased 200%.
* 27% of companies that were victims of Ransomware paid for hackers.
* In the past two years, there have been more than 95 new Ransomware families.
Types of Ransomware
01) Encrypting Ransomware.
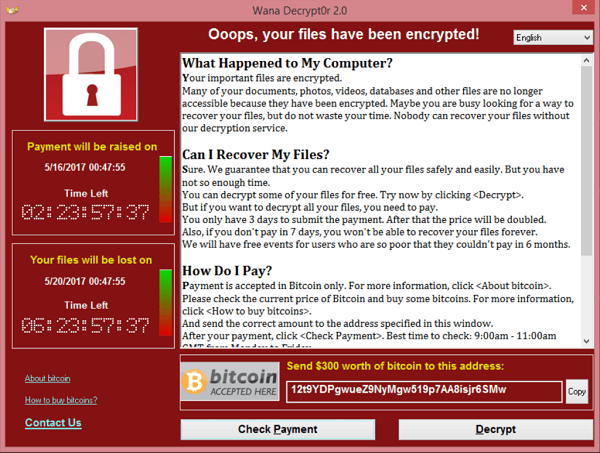
Usually, Ransomware searches for data files such as files with text, images, and pdf files after entry into the user system. It uses complex encryption algorithms (e.g., AES and RSA) to encrypt these files. Cybercriminals will demand that victims pay a specific ransom rate in the form of Bitcoin within a specified period.
Ransomware Encryption does not affect the running of the system. Also, the encryption algorithm selected by Ransomware cannot be cracked, and transactions cannot be traced in electronic currency. (as you know, cryptocurrency wallet cannot trace) With these, all advantages, encrypting Ransomware has become the most popular Ransomware nowadays.
02) Lock-screen Ransomware.
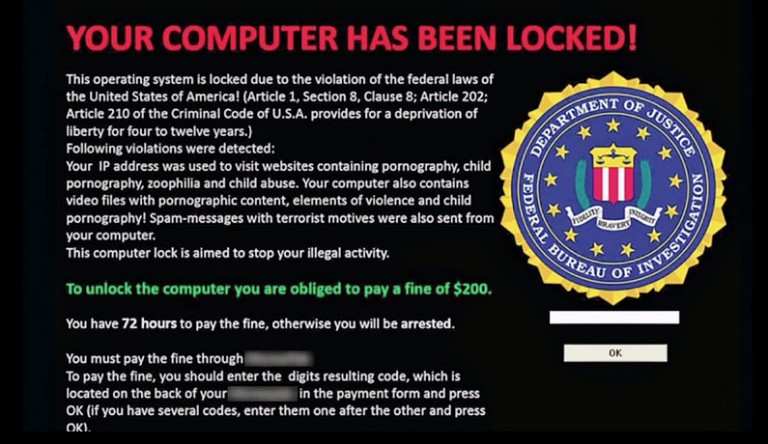
The ransomware lock screen doesn't encrypt files. Instead, it locks operating systems, browsers, or keyboards so that victims are not allowed to use them. The typical WinLock ransomware uses pornographic images for blocking screens for victims until victims send a $10 premium password SMS. Cybercriminals claim they have access to information about the privacy of their victims and, if they do not pay the ransom on time, expose or send data on their privacy on social media. Particular cybercriminals also sell darknet data. Such crimes are particularly harmful and threaten the personal reputation of victims.
How to Prevent Ransomware Attacks?
01) Protection of the network
The key to fighting ransomware attacks is to intercept attacks before they enter the organizations. The best way to avoid the breakdown of an attacker by a simple defense system is to create a multi-layer security defense system using a firewall. The most straightforward and most efficient protection measures are strict security policies. You can enable only necessary services and block the high-risk ports. If you do not secure this way, the attacker can create Ransomware or exploit new vulnerabilities, increasing their costs. Filtering can also be enabled to prevent the entry of high-risk files into the network. URL filtering is used to block malicious websites so that users do not download malware accidentally. The FireHunter, CIS, and deception system can fully detect a safety situation on a highly secure network.
Moreover
* Setting up strict safety policies to limit users' access to networks and apps
* Using the IPS and AV functions, known threats are detected and blocked.
* Implementing a log audit system for investigation, evidence collection, and attack source tracing
02) Host Protection
Firstly, it is suggested that hosts be configured uniformly using an IT infrastructure solution at the organizational level.
Secondly, employee information security training is needed. A large number of Ransomware use email and social engineering to entice employees to download malware.
Moreover
* Updating the system and software patches regularly
* Backing up necessary data regularly
* Installing antivirus software and keeping the virus database up to date
* Software downloaded from the given location only (Trusted source)
* Don't open unknown email attachments or links
* Show extension of the file name - Displaying Windows folder file extensions makes detecting potential malicious files easier. Cybercriminals often use multiple filename extensions to hide malicious files such as videos, pictures, or documents (for example, tax refund.doc.SCR).
References:
Well, Ransomware is a type of malicious software used by cybercriminals to prevent you from accessing your data. The term "ransom" tells you everything you need to know about this pest. That malicious software can encrypt your computer and then demand a ransom to unlock it. And like any other virus, Ransomware also can spread over your network to shared drives, servers, attached computers, and other accessible systems once the initial infection has taken place. If the ransom demands are not met within the timeframe of cyber crooks, the system or the encrypted data is unavailable, or the software can delete your information and eliminate the decrypting key. So without a description key, it is impossible to decrypt the encrypted files. As a result, we can call Ransomware is a potential "nightmare" for unprepared IT peoples.
Ransomware Statistics
* Last year, there were over 304 million ransomware attacks worldwide. Every 11-14 seconds, a new organization is attacked.
* Encrypting data was successful in 73% of all ransomware attacks.
* 55% of attacks targeted businesses with 100 or fewer employees. 75% of attacks targeted companies with less than $50 million in annual revenue.
* Microsoft reports that nearly 97% of all infections in Ransomware take less than 4 hours for their target to be successfully infiltrated. The fastest can take over systems in less than 45 minutes.
* Over the past year, downtime caused by Ransomware increased 200%.
* 27% of companies that were victims of Ransomware paid for hackers.
* In the past two years, there have been more than 95 new Ransomware families.
Types of Ransomware
01) Encrypting Ransomware.
Usually, Ransomware searches for data files such as files with text, images, and pdf files after entry into the user system. It uses complex encryption algorithms (e.g., AES and RSA) to encrypt these files. Cybercriminals will demand that victims pay a specific ransom rate in the form of Bitcoin within a specified period.
Ransomware Encryption does not affect the running of the system. Also, the encryption algorithm selected by Ransomware cannot be cracked, and transactions cannot be traced in electronic currency. (as you know, cryptocurrency wallet cannot trace) With these, all advantages, encrypting Ransomware has become the most popular Ransomware nowadays.
02) Lock-screen Ransomware.
The ransomware lock screen doesn't encrypt files. Instead, it locks operating systems, browsers, or keyboards so that victims are not allowed to use them. The typical WinLock ransomware uses pornographic images for blocking screens for victims until victims send a $10 premium password SMS. Cybercriminals claim they have access to information about the privacy of their victims and, if they do not pay the ransom on time, expose or send data on their privacy on social media. Particular cybercriminals also sell darknet data. Such crimes are particularly harmful and threaten the personal reputation of victims.
How to Prevent Ransomware Attacks?
01) Protection of the network
The key to fighting ransomware attacks is to intercept attacks before they enter the organizations. The best way to avoid the breakdown of an attacker by a simple defense system is to create a multi-layer security defense system using a firewall. The most straightforward and most efficient protection measures are strict security policies. You can enable only necessary services and block the high-risk ports. If you do not secure this way, the attacker can create Ransomware or exploit new vulnerabilities, increasing their costs. Filtering can also be enabled to prevent the entry of high-risk files into the network. URL filtering is used to block malicious websites so that users do not download malware accidentally. The FireHunter, CIS, and deception system can fully detect a safety situation on a highly secure network.
Moreover
* Setting up strict safety policies to limit users' access to networks and apps
* Using the IPS and AV functions, known threats are detected and blocked.
* Implementing a log audit system for investigation, evidence collection, and attack source tracing
02) Host Protection
Firstly, it is suggested that hosts be configured uniformly using an IT infrastructure solution at the organizational level.
Secondly, employee information security training is needed. A large number of Ransomware use email and social engineering to entice employees to download malware.
Moreover
* Updating the system and software patches regularly
* Backing up necessary data regularly
* Installing antivirus software and keeping the virus database up to date
* Software downloaded from the given location only (Trusted source)
* Don't open unknown email attachments or links
* Show extension of the file name - Displaying Windows folder file extensions makes detecting potential malicious files easier. Cybercriminals often use multiple filename extensions to hide malicious files such as videos, pictures, or documents (for example, tax refund.doc.SCR).


References:
https://www.kaspersky.com/resource-center/threats/ransomware


There is no any comment yet! Be the first!